

VulnEscape is a vulnlab machine imported to HackTheBox as a Easy Windows box. I started with network enumeration with nmap, revealing only RDP port running on the target.
I connected to the target with rdesktop which reveals that this box was setup as kiosk machine and I can login as "kioskuser0" without any password to
I escaped kiosk mode by spawning new Microsoft Edge instance that let me download cmd.exe with file protocol which I rename it to msedge.exe to execute and get the command prompt on the box.
Then I discovered Remote Desktop Plus profile which I used Kernel Password Unmask to reveals password of "admin" user in the Remote Desktop Plus application and finally obtain a shell as admin user.
The admin user is in the Administrators group so I started another powershell process with UAC prompt and finally obtain full privileges of this user and root the box.
I start with nmap enumeration as always and as we can see that there is only a single RDP port exposed on this box.
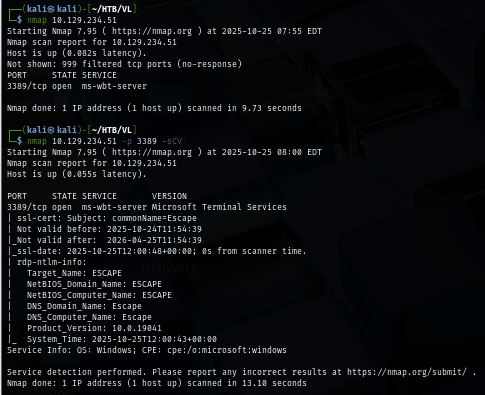
Since I don't have any credential to work on, I will use rdesktop to connect to the box which I discover the username I can use right away upon connecting to the box.
rdesktop $IP
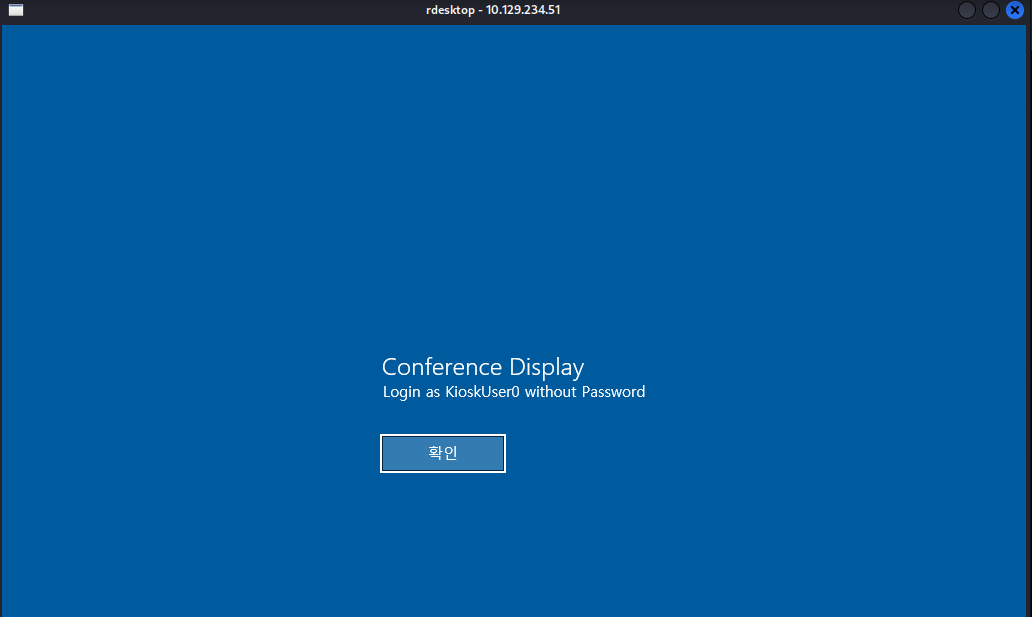
I will login as "KioskUser0" which do not required any password and once I'm in, I can see the display image of a good view and a text in the middle of "Busan Expo" so this machine was setup kiosk mode on KioskUser0 to display specific webpage in Microsoft Edge.

There are couple of way to escape from this restrict environment and first is to press "Windows" button which will open Start Menu.

On this start menu, I try to run cmd.exe but It could not be launched because it was configured to run only msedge.exe in kiosk environment.
I will open another Microsoft Edge instance which will pop up new edge browser but this time, I have access to url bar and several feature of the browser.
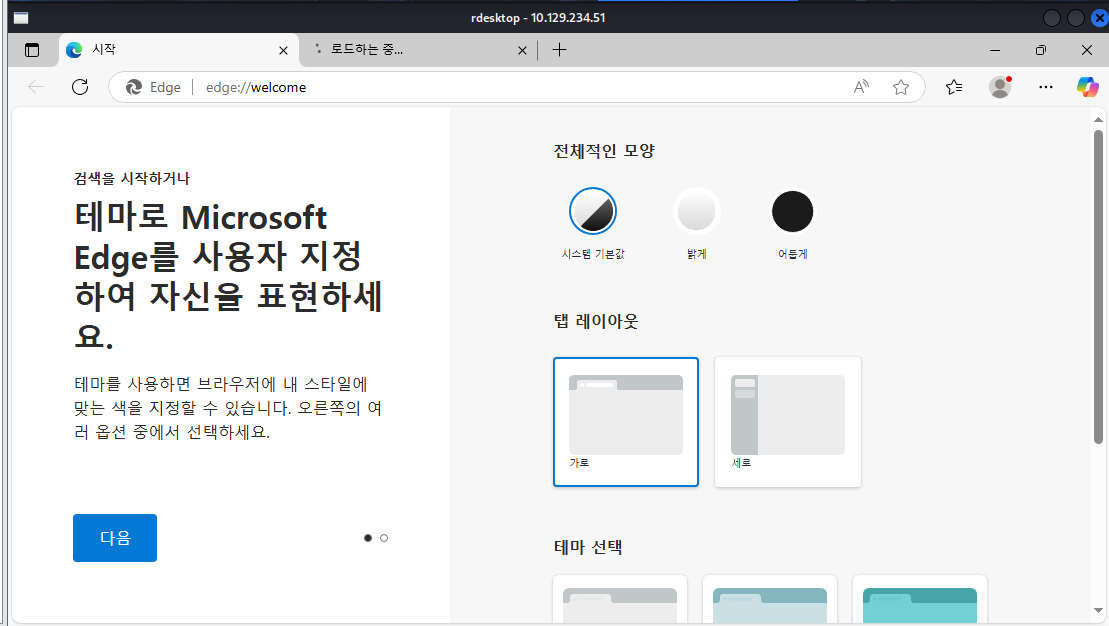
But the new browser instance will also restricted which I can not access other folder beside "Downloads" folder of "KioskUser0" user if I open file explorer windows from "Open", "Save" or even spawn new file explorer so I will use file protocol (file:\\C:) to access the file system as seen in the image below
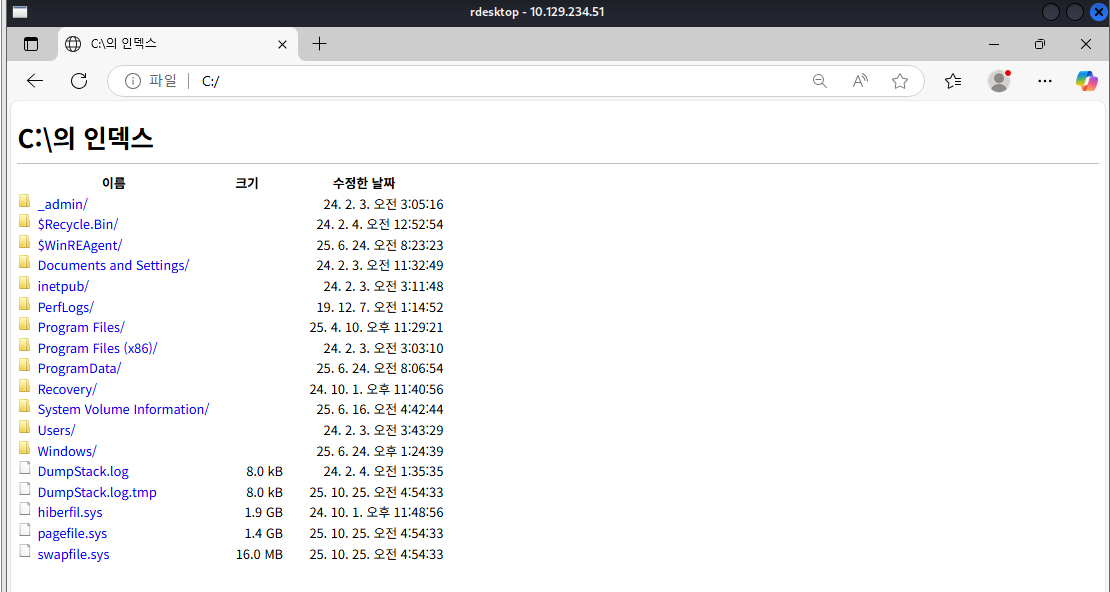
Now I will download cmd.exe from file:\\C:\Windows\System32 to the downloads folder that I can access
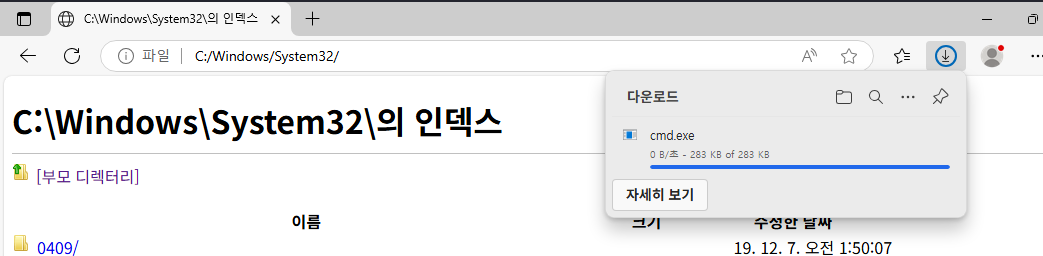
This cmd will not be able to run if I don't change the name to msedge.exe.
So I change the name of cmd.exe to msedge.exe and now I can finally execute it as a new command prompt window pop-up in the full screen but in this command prompt. there are multiple errors message display along with the result of any command I type. (probably because of cmd.exe run outside from the standard environment and even changed its name)
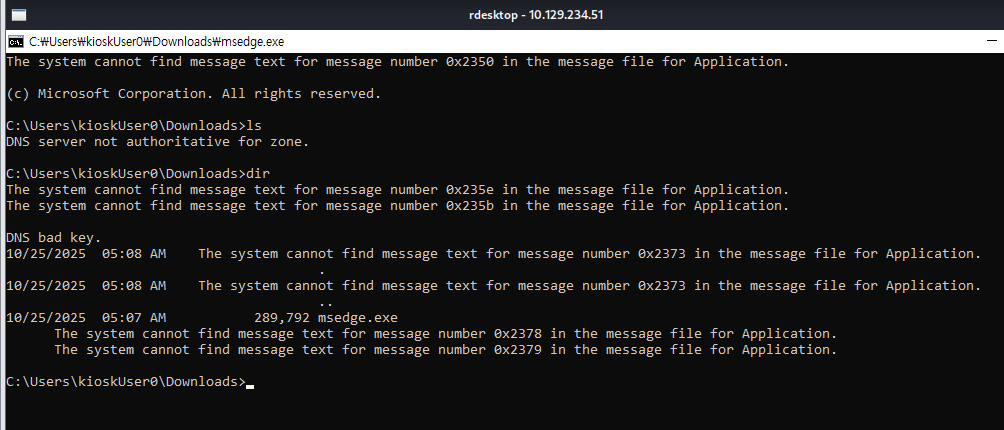
So I will change it to PowerShell since the restriction could not affect here and now all of the output will not have any error messages eariler.
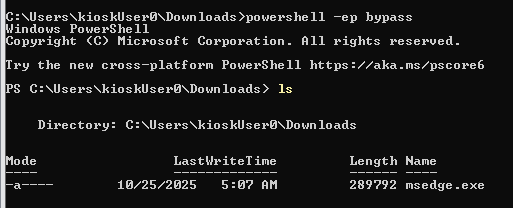
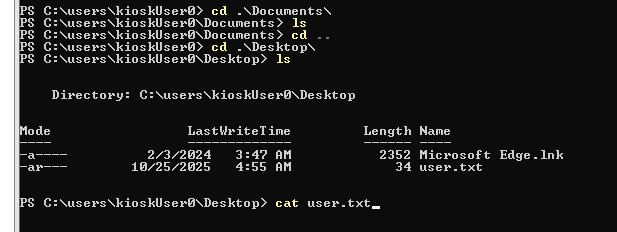
Now I can grab the flag on the desktop of "KioskUser0" user.
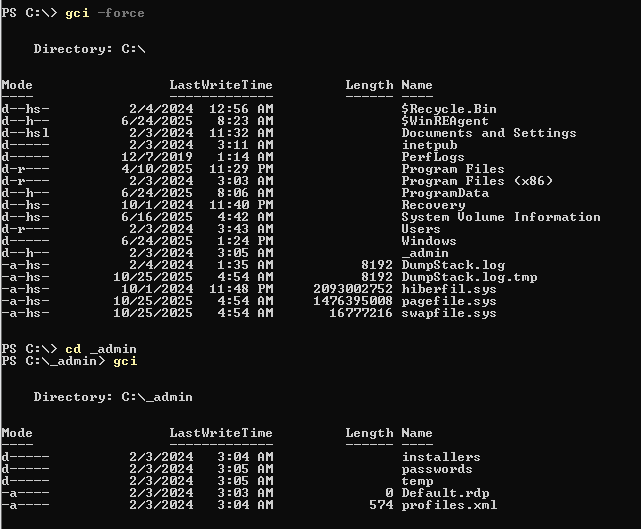
After exploring the file system, I discover _admin folder located at the root of C drive and it contains profiles.xml inside of it.
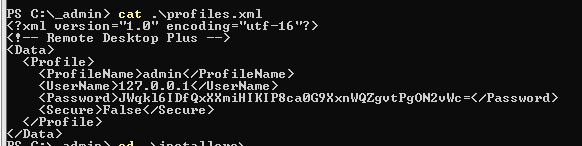
This profile contains encrypted password of "admin" user and it can be used with "Remote Desktop Plus" application so I will find this software and import this profile to see if I can obtain cleartext password.
After exploring the file system again, I found "Remote Desktop Plus" installation folder inside "Program Files (x86)" folder.
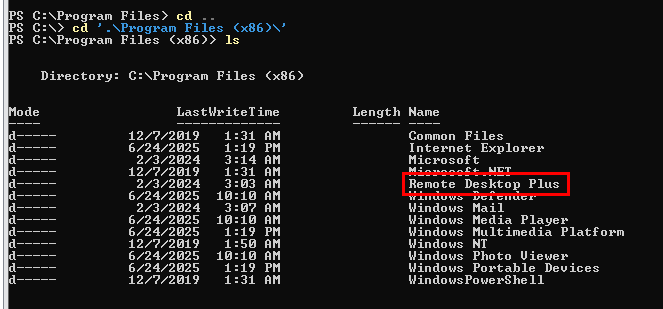
I will execute rdp.exe inside this folder to open Remote Desktop Plus.
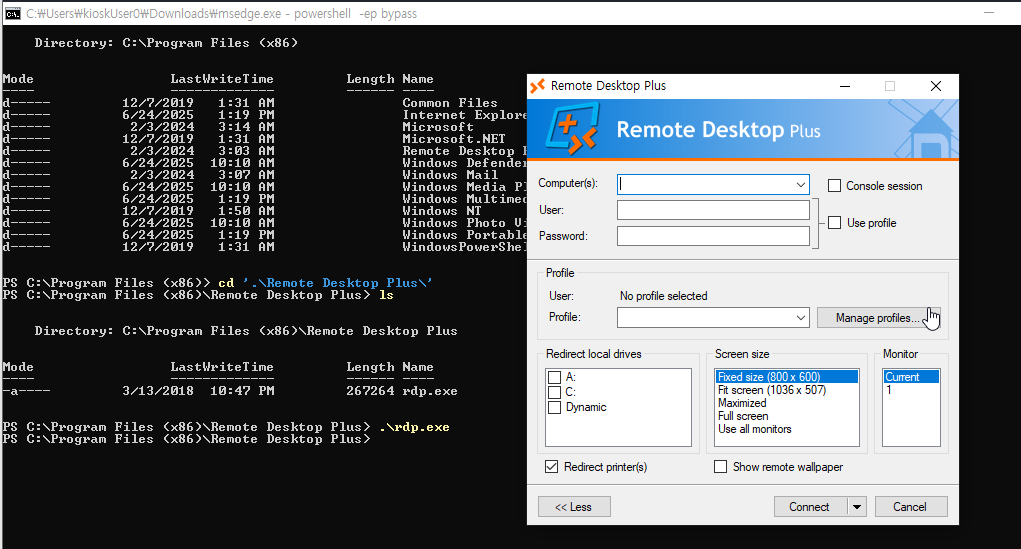
Now I will import the profile, I found in _admin folder into this application.
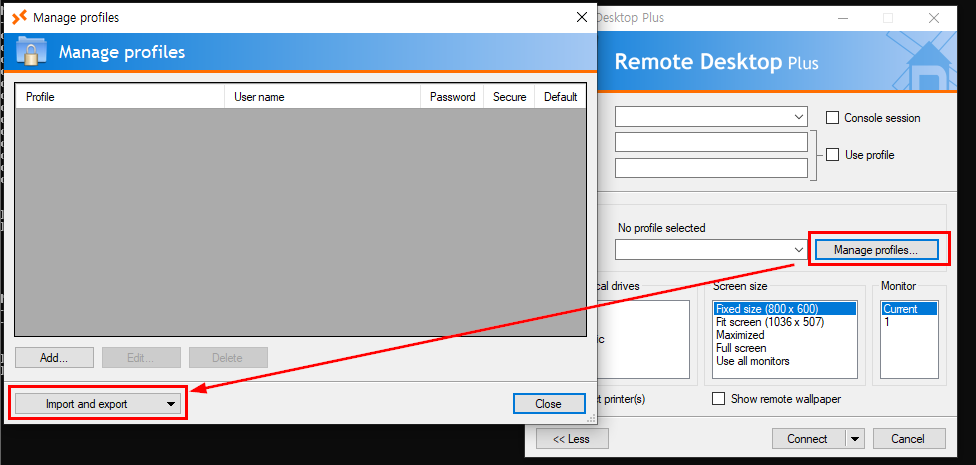
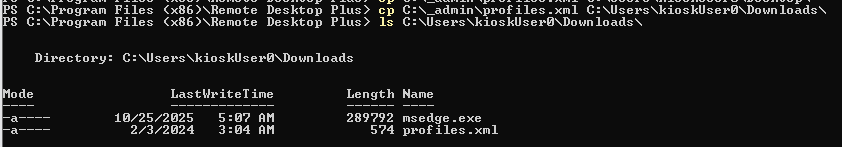
Well look like I still could not access to other folder using File Explorer so I will need to copy the file to Downloads folder so I can import from there.
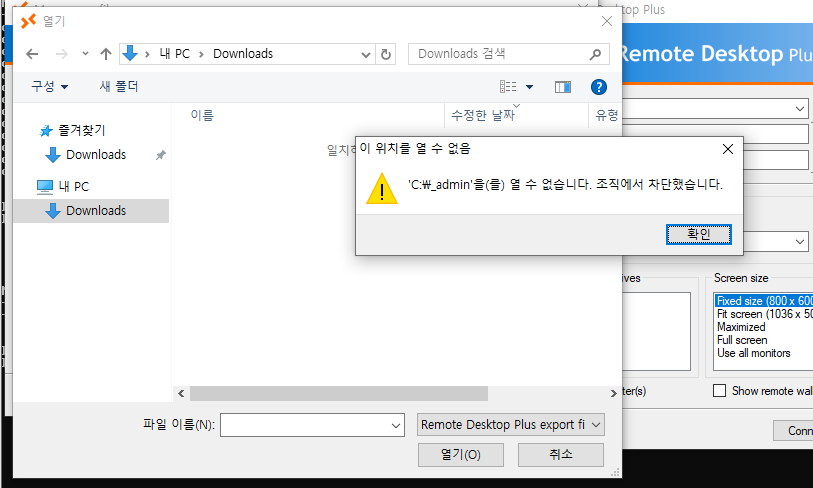
Copy the file to Downloads folder of kioskUser0 user.
cp C:\_admin\profiles.xml C:\Users\kioskUser0\Downloads\
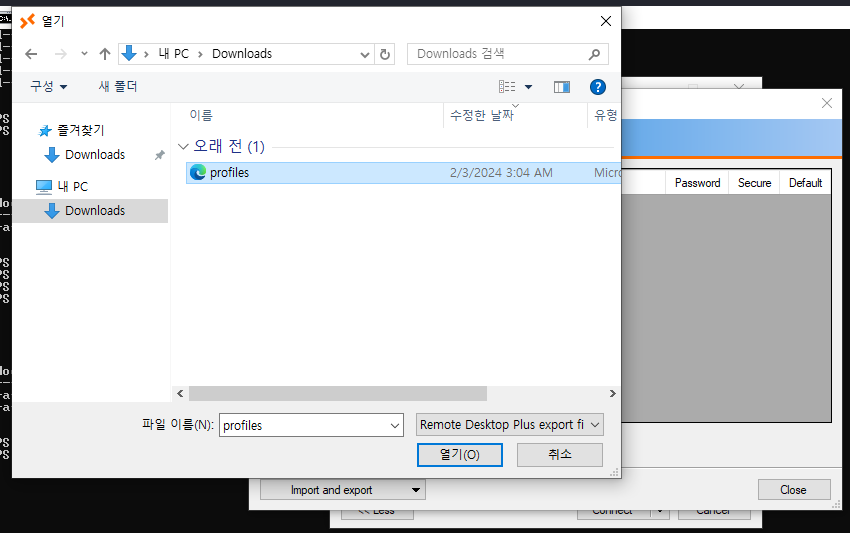
Now I can import this profile.
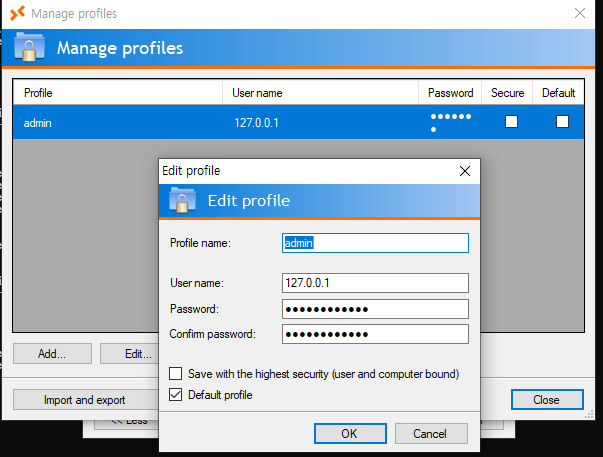
Sadly the password is still marked inside this application so I will need a way to reveal it in cleartext.
First software I think of is the BulletsPassView from Nirsoft so I download it to the box and execute it.
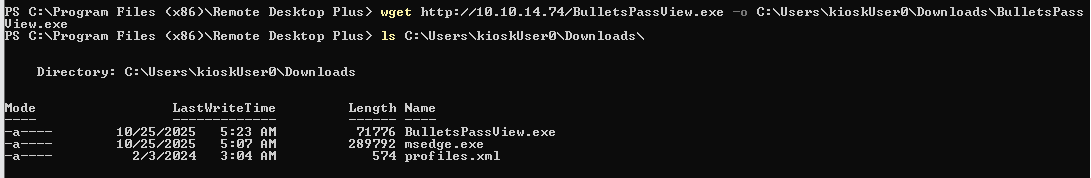
For some reason, It did not recognize the password in Remote Desktop Plus so I will resort with another software.
The next software I will utilize is Kernel Password Unmask that can also unmask the password in GUI application like Remote Desktop Plus.
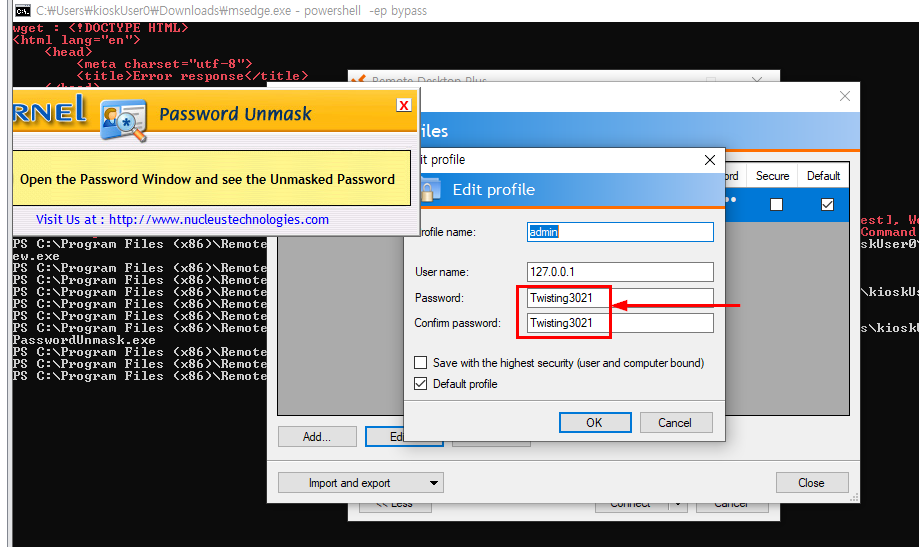
After open the program, I start Remote Desktop Plus again and this time I can finally see the password of admin account (Twisting3021)
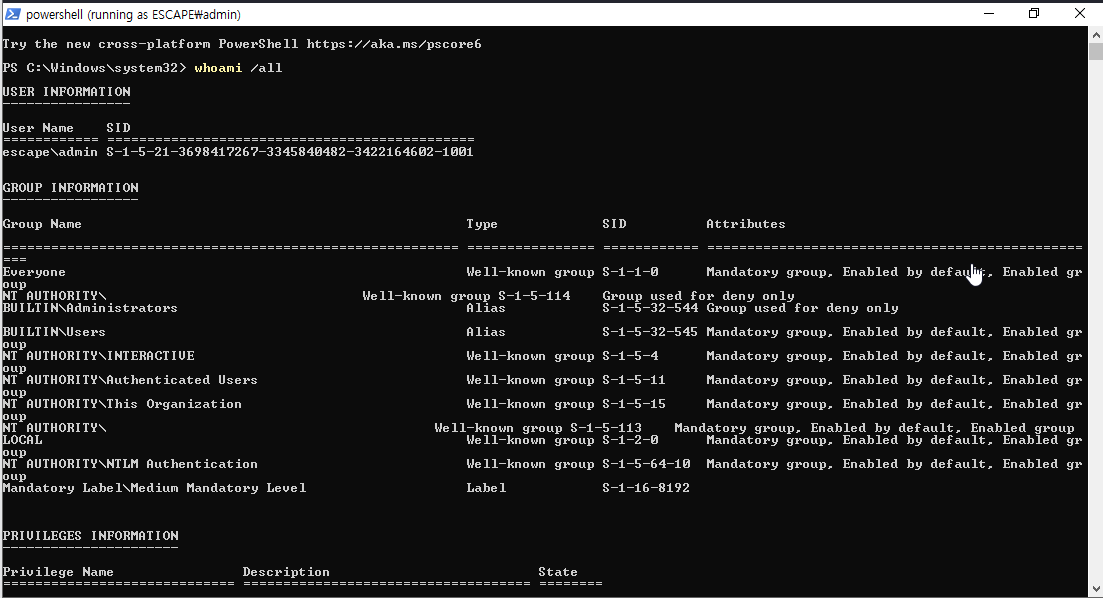
I will use runas command to start a new powershell process in "admin" user context and I found that this user is in the member of Administrators group which I can spawn a new process again to trigger UAC and have full privilege as Administrator.
runas /user:admin powershell
I will use -Verb runas flag of Start-Process cmdlet to spawn PowerShell in administrative context which trigger UAC to prompt.
Start-Process powershell -Verb runas
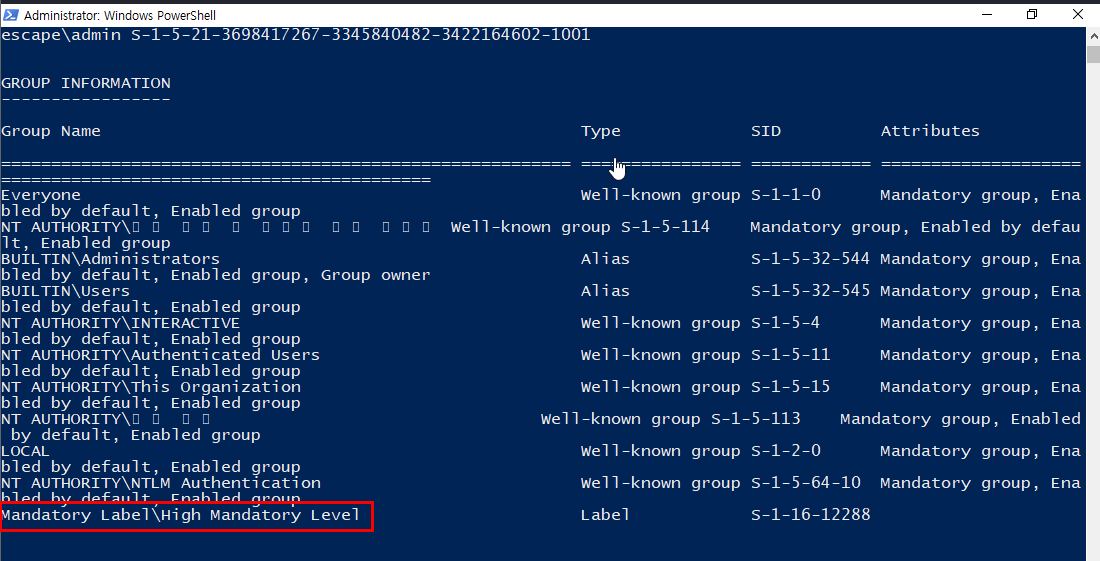
And now I finally have full privilege administrator shell to get the root flag.
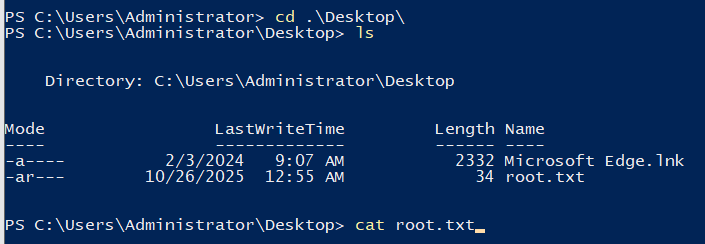
The root flag is located on the desktop of administrator user and I successfully root the box :D
https://labs.hackthebox.com/achievement/machine/1438364/678